Question 1
Which protocol is used to encrypt control plane traffic between SD-WAN controllers and SD-WAN endpoints?
A. DTLS B. IPsec C. PGP D. HTTPS
Answer: A
Explanation
DTLS protocol is used to encrypt control plane traffic between vSmart (controllers) and other SD-WAN endpoints.

Question 2
Which network devices secure API platform?
A. next-generation intrusion detection systems B. Layer 3 transit network devices C. content switches D. web application firewalls
Answer: A
Question 3
An engineer must configure the strongest password authentication to locally authenticate on a router. Which configuration must be used?
A. username netadmin secret 5 $1$bfjk$kdiSiDKKdkXksufZ2 B. username netadmin secret $1$bfjk$kdiSiDKKdkXksufZ2 C. line console 0 password $1$bfjk$k D. username netadmin secret 9 $9$vFpMf83kdDJ9kdjDdjdu/dkfhZiz
Answer: D
Explanation
Best Practices + The enable password command should no longer be used. Use enable secret instead. username joeblow password mypass command should no longer be used. Use username joeblow secret mypass instead. + Type 4 Passwords should never be used! + Use Type 6, Type 8 and Type 9 wherever possible. + Type 0, Type 5 and Type 7 should be migrated to other stronger methods.
Question 4
A network engineer must configure NETCONF. After creating the configuration, the engineer gets output from the command show line, but not from show running-config. Which command completes the configuration?
A. Device(config)# no netconf ssh acl 1 B. Device(config)# netconf max-sessions 100 C. Device(config)# netconf lock-time 500 D. Device(config)# netconf max-message 1000
Answer: C
Explanation
The “netconf lock-time {seconds} specifies the maximum time a NETCONF configuration lock is in place without an intermediate operation.
Question 5
An engineer is configuring a new SSID to present users with a splash page for authentication. Which WLAN Layer 3 setting must be configured to provide this functionally?
A. CCKM B. WPA2 Policy C. Local Policy D. Web Policy
Answer: D
Explanation
In the figure below, we have to tick on “Web Policy” to enable “Splash Page Web Redirect”.

Question 6
An engineer is working with the Cisco DNA Center API. Drag and drop the methods from the left onto the actions that they are used for on the right.
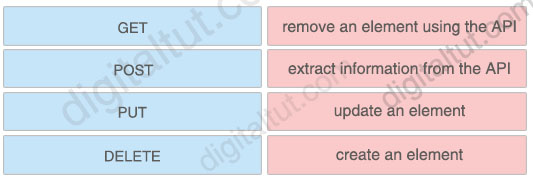
Answer:
+ remove an element using the API: DELETE + extract information from the API: GET + update an element: PUT + create an element: POST
Explanation
A RESTful API uses existing HTTP methodologies defined by the RFC 2616 protocol, such as:
+ GET to retrieve a resource; + PUT to change the state of or update a resource, which can be an object, file or block + POST to create that resource + DELETE to remove it.
Question 7
An engineer must create an EEM script to enable OSPF debugging in the event the OSPF neighborship goes down. Which script must the engineer apply?
| Option A event manager applet ENABLE_OSPF_DEBUG event syslog pattern “%OSPF-5-ADJCHG: Process 6, Nbr 1.1.1.1 on Serial0/0 from FULL to DOWN” action 1.0 cli command “enable” action 2.0 cli command “debug ip ospf event” action 3.0 cli command “debug ip ospf adj” action 4.0 syslog pnonty informational msg “ENABLE_OSPF_DEBUG” |
Option B event manager applet ENABLE OSPF_DEBUG event syslog pattern “%OSPF-5-ADJCHG: Process 5, Nbr 1.1.1.1 on Serial0/0 from LOADING to FULL” action 1.0 cli command “debug ip ospf event” action 2.0 cli command “debug ip ospf adj” action 3.0 syslog priority informational msg “ENABLE_OSPF_DEBUG” |
| Option C event manager applet ENABLE_OSPF_DEBUG event syslog pattern “%OSPF-1-ADJCHG: Process 5, Nbr 1.1.1.1 on Serial0/0 from FULL to DOWN” action 1.0 cli command “debug ip ospf event” action 2.0 cli command “debug ip ospf adj” action 3.0 syslog pnonty informational msg “ENABLE_OSPF_DEBUG |
Option D event manager applet ENABLE_OSPF_DEBUG event syslog pattern “%OSPF-5-ADJCHG: Process 5, Nbr 1.1.1.1 on Serial0/0 from LOADING to FULL” action 1.0 cli command “enable” action 2.0 cli command “debug ip ospf event” action 3.0 cli command “debug ip ospf adj” action 4.0 syslog priority informational msg “ENABLE_OSPF_DEBUG” |
A. Option A
B. Option B
C. Option C
D. Option D
Answer: A
Explanation
This EEM script is only used when OSPF neighborship goes down so the OSPF must be “from FULL to DOWN”, not “from LOADING to FULL” so Option B and Option D are not correct. Also the SEVERITY level of Syslog message of this event is 5 (notification) so it must be “%OSPF-5-ADJCHG”, not “%OSPF-1-ADJCHG” -> Only Option A is correct.
Question 8
A network engineer is adding an additional 10Gbps link to an exiting 2x10Gbps LACP-based LAG to augment its capacity. Network standards require a bundle interface to be taken out of service if one of its member links goes down, and the new link must be added with minimal impact to the production network. Drag and drop the tasks that the engineer must perform from the left into the sequence on the right. Not all options are used.

Answer:
+ Step 1: Validate the physical and data link layers of the 10Gbps link + Step 2: Execute the channel-group number mode active command to add the 10Gbps link to the existing bundle + Step 3: Execute the lacp min-bundle 3 command to set the minimum of ports threshold + Step 4: Validate the network layer of the 10Gbps link
Explanation
“Network standards require a bundle interface to be taken out of service if one of its member links goes down” -> Use the lacp min-bundle command to configure the minimum number of active links allowed in an LACP bundle. When the number of active links falls below this minimum threshold, the port channel shuts down.
LACP is used so we must configure the new port with “channel-group number mode active” command before setting the limitation of 3 ports or the Etherchannel link would go down.
Question 9
An engineer is implementing a route map to support redistribution within BGP. The route map must configured to permit all unmatched routes. Which action must the engineer perform to complete this task?
A. Include a permit statement as the first entry B. Include at least one explicit deny statement C. Remove the implicit deny entry D. Include a permit statement as the last entry
Answer: D
Question 10
Drag and drop the snippets onto the blanks within the code to construct a script that configures BGP according to the topology. Not all options are used, and some options may be used twice.

Answer:
1. 65001 2. 192.168.1.1 3. 65000 4. 192.168.1.1
Explanation
This question did not tell us which router we are configuring so we suppose we are configuring Client router (which is more reasonable). Therefore in the first box we have to enter the BGP AS number (same as “router bgp {as-number}” command).
In the second and third box we have to configure BGP neighbor information (same as “neighbor {neighbor-IP-address} remote-as {remote-as}” command).
In the last box we have to configure under “address-family ipv4” mode so we need to type the neighbor IP address once more.
======================= New Questions (added on 17th-Sep-2021) =======================
Question 11
Refer to the exhibit.
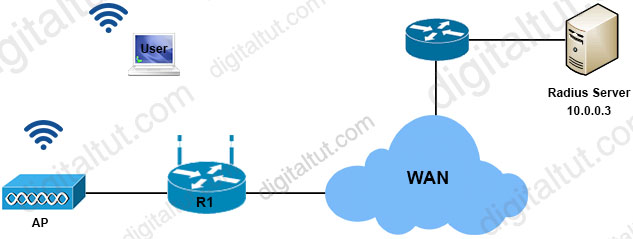
| AP(config)# aaa group server radius rad_auth AP(config-sg-radius)# server 10.0.0.3 auth-port 1645 acct-port 1646 AP(config)# aaa new-model AP(config)# aaa authentication login eap_methods group rad_auth AP(config)# radius-server host 10.0.0.3 auth-port 1645 acct-port 1646 key labapl200 AP(config)# interface dot11radio 0 AP(config-if)# ssid labap1200 AP(config-if-ssid)# encryption mode wep mandatory |
A company requires that all wireless users authenticate using dynamic key generation. Which configuration must be applied?
A. AP(config-if-ssid)# authentication open wep wep_methods
B. AP(config-if-ssid)# authentication dynamic wep wep_methods
C. AP(config-if-ssid)# authentication dynamic open wep_dynamic
D. AP(config-if-ssid)# authentication open eap eap_methods
Answer: D
Explanation
When your SSID authentication mechanism uses Extensible Authentication Protocol (EAP) with 802.1x authentication (and without WPA v1 or WPA v2 support), dynamic WEP keys can be generated for each wireless user. Dynamic WEP keys are more secure than static, or unchanging, WEP keys. If an intruder passively receives enough packets encrypted by the same WEP key, the intruder can perform a calculation to learn the key and use it to join your network. Because they change frequently, dynamic WEP keys prevent intruders from performing the calculation and learning the key.
Question 12
Which threat defense mechanism, when deployed at the network perimeter, protects against zero-day attacks?
A. intrusion prevention
B. stateful inspection
C. sandbox
D. SSL decryption
Answer: D
Explanation
When your SSID authentication mechanism uses Extensible Authentication Protocol (EAP) with 802.1x authentication (and without WPA v1 or WPA v2 support), dynamic WEP keys can be generated for each wireless user. Dynamic WEP keys are more secure than static, or unchanging, WEP keys. If an intruder passively receives enough packets encrypted by the same WEP key, the intruder can perform a calculation to learn the key and use it to join your network. Because they change frequently, dynamic WEP keys prevent intruders from performing the calculation and learning the key.
Question 12
Which threat defense mechanism, when deployed at the network perimeter, protects against zero-day attacks?
A. intrusion prevention
B. stateful inspection
C. sandbox
D. SSL decryption
Answer: D
Explanation
There are two types of hypervisors: type 1 and type 2 hypervisor.
In type 1 hypervisor (or native hypervisor), the hypervisor is installed directly on the physical server. Then instances of an operating system (OS) are installed on the hypervisor. Type 1 hypervisor has direct access to the hardware resources. Therefore they are more efficient than hosted architectures. Some examples of type 1 hypervisor are VMware vSphere/ESXi, Oracle VM Server, KVM and Microsoft Hyper-V.
In contrast to type 1 hypervisor, a type 2 hypervisor (or hosted hypervisor) runs on top of an operating system and not the physical hardware directly. A big advantage of Type 2 hypervisors is that management console software is not required. Examples of type 2 hypervisor are VMware Workstation (which can run on Windows, Mac and Linux) or Microsoft Virtual PC (only runs on Windows).

Question 14
Which two items are found in YANG data models? (Choose two)
A. HTTP return codes
B. rpc statements
C. JSON schema
D. container statements
E. XML schema
Answer: B D
Explanation
The following YANG example uses a container statement to define a timeout mechanism for a request to a server. The timeout has two components: access-timeout, which represents the maximum time without server response, and retries, which represents the number of request attempts before giving up.
container timeout {
leaf access-timeout {
type uint32;
}
leaf retries {
type uint8;
}
}
Reference: https://www.tail-f.com/wordpress/wp-content/uploads/2014/02/Tail-f-Instant-YANG.pdf
IOS XR actions are RPC statements that trigger an operation or execute a command on the router. Theses actions are defined as YANG models using RPC statements. An action is executed when the router receives the corresponding NETCONF RPC request. Once the router executes an action, it replies with a NETCONF RPC response.
Note: A data model is simply a well understood and agreed upon method to describe “something”. As an example, consider this simple “data model” for a person. Person •Gender-male, female, other •Height-Feet/Inches or Meters •Weight-Pounds or Kilos
•Hair Color-Brown, Blond, Black, Red, other •Eye Color-Brown, Blue, Green, Hazel, other
Question 15
What is a characteristic of Cisco DNA Northbound APIs?
A. They utilize RESTCONF
B. They enable automation of network infrastructure based on intent
C. They simplify the management of network infrastructure devices
D. They utilize multivendor support APIs
Answer: B
Explanation
Software-Defined Access (SDA) uses the software-defined architectural model, with a controller and various APIs. At the center sits the Digital Network Architecture (DNA) Center controller. DNA Center is the controller for SDA networks.
'보안 > 이론' 카테고리의 다른 글
| [CCNP] New ENCOR Questions Part 7-3 (0) | 2021.11.12 |
|---|---|
| [CCNP] New ENCOR Questions Part 7-2 (0) | 2021.11.12 |
| [CCNP]New ENCOR Questions Part 7-1 (1) | 2021.11.12 |
| 네트워크 기초 공부 자료 (0) | 2021.11.11 |
| 재택근무 시 지켜야 할 정보보호 6대 실천 수칙 (0) | 2021.10.18 |
