New ENCOR Questions- Part 7
Question 1
An engineer must export the contents of the devices object in JSON format. Which statement must be use?

A. json.print(Devices)
B. json.loads(Devices)
C. json.dumps(Devices)
D. json.repr(Devices)
Answer: C
Explanation
json.loads() takes in a string and returns a json object while json.dumps() takes in a json object and returns a string. In this question, “Devices” is a ‘list’, not a string so we have to “dumps” it first to convert it into a string before printing it out.
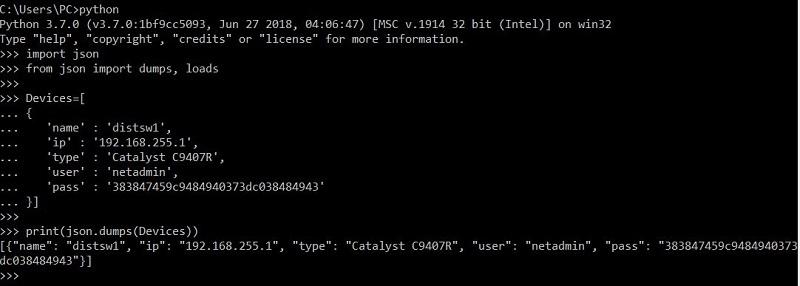
Try printing with “loads”:

Note: JSON does not have attributes “print” or “repr” so we cannot use them.
Question 2
What is the function of Cisco DNA Center in a Cisco SD-Access deployment?
A. It is responsible for routing decisions inside the fabric
B. It is responsible for the design, management, provisioning, and assurance of the fabric network devices
C. It possesses information about all endpoints, nodes, and external networks related to the fabric
D. It provides integration and automation for all nonfabric nodes and their fabric counterparts
Answer: B
Question 3
Refer to the exhibit

An engineer troubleshoots connectivity issues with an application. Testing is performed from the server gateway, and traffic with the DF bit set is dropped along the path after increasing packet size. Removing the DF bit setting at the gateway prevents the packets from being dropped. What is the cause of this issue?
A. PMTUD does not work due to ICMP Packet Too Big messages being dropped by an ACL
B. The remote router drops the traffic due to high CPU load
C. The server should not set the DF bit in any type of traffic that is sent toward the network
D. There is a CoPP policy in place protecting the WAN router CPU from this type of traffic
Answer: C
Explanation
If the DF bit is set, routers cannot fragment packets. The ping result of “MMMMM” means “Maximum transmission unit (MTU) problem. Could not fragment.” -> In this case, packet needs to be fragmented but we disabled fragmentation via DF bit.
Question 4
Refer to the exhibit.
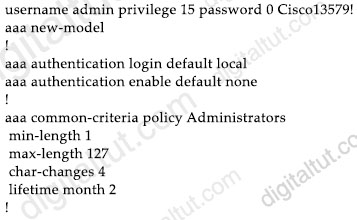
A network engineer must configure a password expiry mechanism on the gateway router for all local passwords to expire after 60 days. What is required to complete this task?
A. Add the username admin privilege 15 common-criteria-policy Administrators password 0 Cisco013579! command B. No further action is required. The configuration is complete
C. Add the aaa authentication enable default Administrators command
D. The password expiry mechanism is on the AAA server and must be configured there
Answer: A
Explanation
The command “username username common-criteria-policy policy-name password password” applies a specific policy and password to a user profile.
Question 5
Refer to the exhibit.
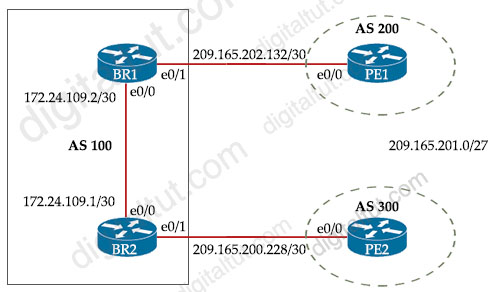
| BR1 router bgp 100 neighbor 172.24.109.1 remote-as 100 neighbor 172.24.109.1 next-hop self neighbor 209.165.202.134 remote-as 200 | PE1 router bgp 200 bgp log-neighbor-changes neighbor 209.165.202.133 remote as 100 |
| BR2 router bgp 100 neighbor 172.24.109.2 remote-as 100 neighbor 172.24.109.2 next-hop-self neighbor 209.165.200.230 remote-as 300 | PE2 router bgp 300 bgp log-neighbor-changes neighbor 209.165.200.229 remote as 100 |
BR2#sh ip route | i 209.165.201.0
209.165.201.0/27 is subnetted, 1 subnets
B 209.165.201.0 [20/0] via 209.165.200.230, 00:00:12
Which configuration change will force BR2 to reach 209.165.201.0/27 via BR1?
A. Set the origin to igp on BR2 toward PE2 inbound B. Set the local preference to 150 on PE1 toward BR1 outbound C. Set the weight attribute to 65,535 on BR1 toward PE1 D. Set the MED to 1 on PE2 toward BR2 outbound
Answer: D
Explanation
We cannot set the local preference on PE1 because local preference is only sent to iBGP neighbors so this attribute cannot reach BR1 -> Answer B is not correct.
Weight attribute is only used locally in a router (not be exchanged between BGP neighbors) so we cannot affect BR2 from BR1 with this attribute -> Answer C is not correct.
We cannot affect BR2 routing decision by modifying BGP advertisements from BR2 toward PE2 (inbound) -> A is not correct. Also if network 209.165.201.0/27 is advertised with “network” statement in BGP, BR2 will match it with origin “IGP”. Please check the example in the link below.
By default, the MED attribute is set to 0 so by increasing the MED on PE2 toward BR2, BR2 would think the metric of its direct link to PE2 is higher than the path advertised by BR1 -> BR2 would use BR1 to reach 209.165.201.0/27.
Good lab example and reference: https://www.cisco.com/c/en/us/support/docs/ip/border-gateway-protocol-bgp/13759-37.html
Question 6
What are two benefits of YANG? (Choose two)
A. It collects statistical constraint analysis information B. In enforces the use of specific encoding format for NETCONF C. In enforces configuration semantics D. It enables multiple leaf statements to exist within a leaf list E. It enforces configuration constraints
By default, the MED attribute is set to 0 so by increasing the MED on PE2 toward BR2, BR2 would think the metric of its direct link to PE2 is higher than the path advertised by BR1 -> BR2 would use BR1 to reach 209.165.201.0/27.
Good lab example and reference: https://www.cisco.com/c/en/us/support/docs/ip/border-gateway-protocol-bgp/13759-37.html
Question 6
What are two benefits of YANG? (Choose two)
A. It collects statistical constraint analysis information B. In enforces the use of specific encoding format for NETCONF C. In enforces configuration semantics D. It enables multiple leaf statements to exist within a leaf list E. It enforces configuration constraints

An engineer configures VRRP and issues the show commands to verify operation. What does the engineer confirm about VRRP group 1 from the output?
A. There is no route to 10.10.1.1/32 in R2’s routing table B. If R1 reboots, R2 becomes the master virtual router until R2 reboots C. Communication between VRRP members is encrypted using MD5 D. R1 is master if 10.10.1.1/32 is in its routing table
Answer: D
Explanation
We don’t have any information about the route to 10.10.1.1/32 so we cannot say if answer A is correct or not.
Answer B is not correct because if R2 reboots, R2 only becomes the master until R1 is up again (not until R2 reboots) because “preempt” is enabled by default with VRRP.
Answer C is not correct because R1 & R2 are authenticating via plain text, not MD5.
R1 is tracking the route to 10.10.1.1/32, if this route is removed from R1’s routing table, the VRRP priority of R1 would be decreased by 20 (110 – 20 = 90) which is smaller than the priority of R2 -> R2 would take the master role -> Answer D is correct.
Question 8
Refer to the exhibit.
flow record Recorder
match ipv4 protocol
match ipv4 source address
match ipv4 destination address
match transport source-port
match transport destination-port
!
flow exporter Exporter
destination 192.168.100.22
transport udp 2055
!
flow monitor Monitor
exporter Exporter
record Recorder
!
et-analytics
ip flow-export destination 192.168.100.22 2055
!
interface gi1
ip flow monitor Monitor input
ip flow monitor Monitor output
et-analytics enable
!
An engineer must add the SNMP interface table to the NetFlow protocol flow records. Where should the SNMP table option be added?
A. under the interface B. under the flow record C. under the flow monitor D. under the flow exporter
Answer: D
Question 9
Refer to the exhibit.
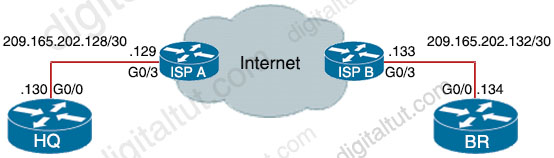
| BR(config)#interface tunnel1 BR(config-if)#keepalive 5 3 HQ(config)#interface tunnel1 HQ(config-if)#keepalive 5 3 |
What is the effect of these commands on the BR and HQ tunnel interfaces?
A. The tunnel line protocol goes down when the keepalive counter reaches 6 B. The keepalives are sent every 5 seconds and 3 retries C. The keepalives are sent every 3 seconds and 5 retries. D. The tunnel line protocol goes down when the keepalive counter reaches 5
Answer: B
Explanation
The syntax of keepalive command is: keepalive {seconds retries} so R1 will send keepalive message every 5 seconds and retry 3 times. If all of the keepalive messages are failed, R1 concludes the tunnel was broken.
Question 10
In Cisco SD-WAN, which protocol is used to measure link quality?
A. OMP B. BFD C. RSVP D. IPsec
Answer: B
Question 11
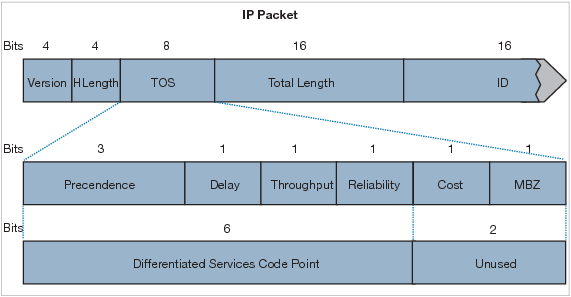
What is used to perform QoS packet classification?
A. the Options field in the Layer 3 header B. the Type field in the Layer 2 frame C. the Flags field in the Layer 3 header D. the ToS field in the Layer 3 header
Answer: D
Explanation
Layer-3 marking is accomplished using the 8-bit Type of Service (ToS) field, part of the IP header. A mark in this field will remain unchanged as it travels from hop-to-hop, unless a Layer-3 device is explicitly configured to overwrite this field. There are two marking methods that use the ToS field: + IP Precedence: uses the first three bits of the ToS field. + Differentiated Service Code Point (DSCP): uses the first six bits of the ToS field. When using DSCP, the ToS field is often referred to as the Differentiated Services (DS) field
Question 12
Refer to the exhibit.
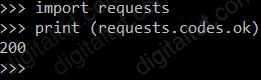
def get_token():
device_url="https://192.168.1.1/dna/sytem/api/v1/auth/token"
http_result = requests.post(device_url, auth = ("test","test34393838!"))
if http_result.status_code != requests.codes.ok:
print("Call failed!" Review get_token().")
sys.exit()
return(http_result.json()["Token"])
Which HTTP code must be returned to prevent the script from exiting?
A. 200 B. 201 C. 300 D. 301
Answer: A
Explanation
In order to prevent the script from exiting, the returned code must equal to “requests.codes.ok” so that the “sys.exit()” statement does not run. “requests.codes.ok” here is 200:
Question 13
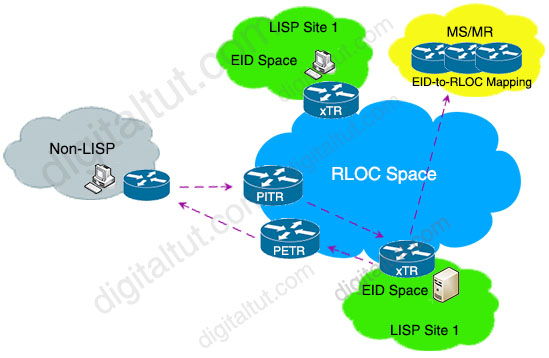
Which LISP component is required for a LISP site to communicate with a non-LISP site?
A. ETR B. ITR C. Proxy ETR D. Proxy ITR
Answer: C
Explanation
The proxy egress tunnel router (PETR) allows the communication from the LISP sites to the non-LISP sites. The PETR receives LISP encapsulated traffic from ITR.
Question 14
What is a characteristic of a next-generation firewall?
A. only required at the network perimeter B. required in each layer of the network C. filters traffic using Layer 3 and Layer 4 information only D. provides intrusion prevention
Answer: D
Question 15
Which technology is used as the basis for the Cisco SD-Access data plane?
A. IPsec B. LISP C. VXLAN D. 802.1Q
Answer: C
Question 16
“HTTP/1.1 204 content” is returned when cur -l -x DELETE command is issued. Which situation has occurred?
A. The object could not be located at the URI path B. The command succeeded in deleting the object C. The object was located at the URI, but it could not be deleted D. The URI was invalid
Answer: B
Explanation
The HTTP 204 No Content success status response code indicates that a request has succeeded, but that the client doesn’t need to navigate away from its current page.
Question 17
An engineer must provide wireless converge in a square office. The engineer has only one AP and believes that it should be placed it in the middle of the room. Which antenna type should the engineer use?
A. directional B. polarized C. Yagi D. omnidirectional
Answer: D
Explanation
Types of external antennas: + Omnidirectional: Provide 360-degree coverage. Ideal in houses and office areas + Directional: Focus the radio signal in a specific direction. Examples are the Yagi and parabolic dish + Multiple Input Multiple Output (MIMO) – Uses multiple antennas (up to eight) to increase bandwidth
An omnidirectional antenna is designed to provide a 360-degree radiation pattern. This type of antenna is used when coverage in all directions from the antenna is required.

Omnidirectional Antenna Radiation Pattern
Question 18
While configuring an IOS router for HSRP with a virtual IP of 10.1.1.1, an engineer sees this log message:
| Jan 1 12:12:14.122: %HSRP-4-DIFFVIP1: GigabitEthernet0/0 Grp 1 active routers virtual IP address 10.1.1.1 is different to the locally configured address 10.1.1.25 |
Which configuration change must the engineer make?
A. Change the HSRP group configuration on the remote router to 1 B. Change the HSRP virtual address on the local router to 10.1.1.1 C. Change the HSRP virtual address on the remote router to 10.1.1.1 D. Change the HSRP group configuration on the local router to 1
Answer: B
Explanation
The local router was configured with command “standby 1 ip 10.1.1.25” while the peer HSRP router was configured with command “standby 10 ip 10.1.1.1”
Question 19
What is a characteristic of YANG?
A. It is a Cisco proprietary language that models NETCONF data B. It allows model developers to create custom data types C. It structures data in an object-oriented fashion to promote model reuse D. It provides loops and conditionals to control now within models
Answer: C
Question 20
What is the function of the LISP map resolver?
A. to send traffic to non-LISP sites when connected to a service provider that does not accept nonroutable EIDs as packet sources B. to connect a site to the LISP-capable part of a core network, publish the EID-to-RLOC mappings for the site and respond to map-request messages C. to decapsulate map-request messages from ITRs and forward the messages to the MS D. to advertise routable non-USP traffic from one address family to LISP sites in a different address family
Answer: C
Explanation
Map Resolver (MR): a LISP component which accepts LISP Encapsulated Map Requests, typically from an ITR, quickly determines whether or not the destination IP address is part of the EID namespace
Question 21
When is an external antenna used inside a building?
A. only when using 5 GHz B. only when using 2.4 GHz C. when it provides the required coverage D. only when using Mobility Express
Answer: C
Question 22
Drag and drop the snippets onto the blanks within the code construct a script that configure a loopback interface with an IP address. Not all options are used.
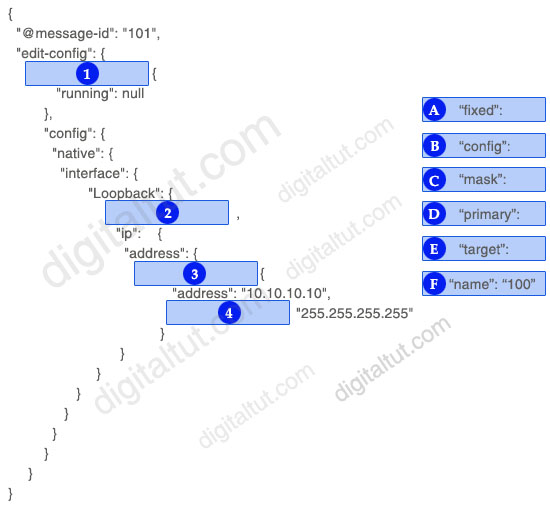
Answer:
1 – E 2 – F 3 – D 4 – C
Explanation
The code above is written in NETCONF with JSON format.
Question 23
Drag and drop the characteristics from the left onto the orchestration tools they describe on the right.
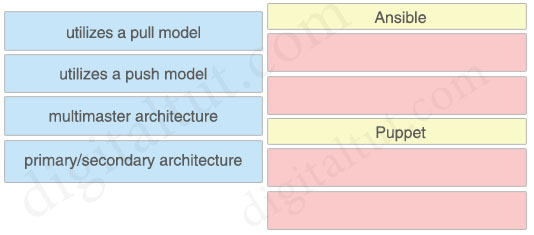
Answer:
Ansible + utilizes a push model + primary/secondary architecture
Puppet + utilizes a pull model + multimaster architecture
Explanation
Ansible runs with a single active node, called the Primary instance. If the primary goes down, there is a Secondary instance to take its place.
Puppet has multi-master architecture. If the active master goes down, then the other master takes the active master place.
Reference: https://www.javatpoint.com/ansible-vs-puppet
Question 24
Refer to the exhibit.

How was spanning-tree configured on this interface?
A. By entering the command spanning-tree portfast trunk in the interface configuration mode. B. By entering the command spanning-tree portfast in the interface configuration mode C. By entering the command spanning-tree mst1 vlan 10,20,30,40 in the global configuration mode D. By entering the command spanning-tree vlan 10,20,30,40 root primary in the interface configuration mode
Answer: A
Explanation
As we see in the output, the type of this interface in all VLANs are “Edge” (which automatically transitions the port to the spanning tree forwarding state without passing through the blocking or learning states) so maybe this interface was configured with “portfast” command. There are many VLANs on this single interface so we can deduce it is a trunk port. Therefore the best answer here should be the command “spanning-tree portfast trunk” has been entered.
Question 25
An engineer is troubleshooting the AP join process using DNS. Which FQDN must be resolvable on the network for the access points to successfully register to the WLC?
A. cisco-capwap-controller.domain.com B. wlchostname.domain.com C. ap-manager.domain.com D. primary-wlc.domain.com
Answer: A
Explanation
The lightweight access points support the following controller discovery processes: … DNS discovery—The access point can discover controllers through your domain name server (DNS). You must configure your DNS to return controller IP addresses in response to CISCO-CAPWAP-CONTROLLER.localdomain, where localdomain is the access point domain name. When an access point receives an IP address and DNS information from a DHCP server, it contacts the DNS to resolve CISCO-CAPWAP-CONTROLLER.localdomain. When the DNS sends a list of controller IP addresses, the access point sends discovery requests to the controllers.
Question 26
How is Layer 3 roaming accomplished in a unified wireless deployment?
A. An EoIP tunnel is created between the client and the anchor controller to provide seamless connectivity as the client is associated with the new AP B. The client entry on the original controller is passed to the database on the new controller C. The new controller assigns an IP address from the new subnet to the client D. The client database on the original controller is updated the anchor entry, and the new controller database is updated with the foreign entry.
Answer: B
Explanation
An EoIP tunnel is created between the anchor and foreign controller, not between the client and the anchor controller -> Answer A is not correct.
In instances where the client roams between APs that are connected to different WLCs and the WLC WLAN is connected to a different subnet, a Layer 3 roam is performed, and there is an update between the new WLC (foreign WLC) and the old WLC (anchor WLC) mobility databases -> Answer B is correct.
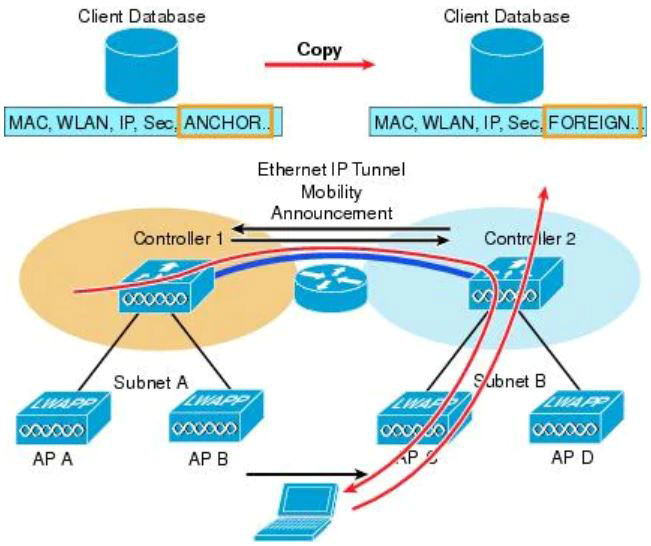
The client begins with a connection to AP B on WLC 1. This creates an ANCHOR entry in the WLC client database (-> Answer D is not correct as the client database is already “ANCHOR”). As the client moves away from AP B and makes an association with AP C, WLC 2 sends a mobility announcement to peers in the mobility group looking for the WLC with the client MAC address. WLC 1 responds to the announcement, handshakes, and ACKs. Next the client database entry for the roaming client is copied to WLC 2, and marked as FOREIGN. Included PMK data (master key data from the RADIUS server) is also copied to WLC 2. This provides fast roam times for WPA2/802.11i clients because there is no need to re-authenticate to the RADIUS server.
After a simple key exchange between the client and AP, the client is added to the WLC 2 database and is similar, except that it is marked as FOREIGN.
Reference: https://www.cisco.com/en/US/docs/solutions/Enterprise/Mobility/emob30dg/TechArch.html
In Layer 3 roaming, no IP address refresh needed (although client must be re-authenticated and new security session established) -> Answer C is not correct.
'보안 > 이론' 카테고리의 다른 글
| [CCNP] New ENCOR Questions Part 7-3 (0) | 2021.11.12 |
|---|---|
| [CCNP] New ENCOR Questions Part 7-2 (0) | 2021.11.12 |
| [CCNP]New ENCOR Questions Part 8 (0) | 2021.11.12 |
| 네트워크 기초 공부 자료 (0) | 2021.11.11 |
| 재택근무 시 지켜야 할 정보보호 6대 실천 수칙 (0) | 2021.10.18 |
